How to Remove WannaLocker Ransomware Manual Removal Guide
Remove WannaLocker ransomware
Tips on removing the WannaLocker (uninstalling WannaLocker ransomware)
WannaLocker is an imposter of the WannaCry ransomware. Currently, it targets Android users in China. However, malware could expand its target field and target computer users around the world. The virus spreads like a plugin for the popular Chinese game in the game forums. On the affected device, ransomware replaces the wallpaper to the image of the anime. Then, it encrypts targeted files with AES encryption and adds a unique file extension that matches the string of random symbols. Once all files are encrypted, the malicious software runs a ransom demanding window that resembles WannaCry. It provides information on the encrypted data and the possibilities of retrieving it in the Chinese language.
WannaLocker ransomware asks to pay 40 Chinese Renminbi and contact them as soon as the transaction is made. They will provide the necessary decryption keys and free games for corrupt files. Meanwhile, two timers in the ransom note show how much time has left up to double the size of the ransom and when users lose their files entirely. However, instead of following these instructions and rushing to make the payment, victims should focus on WannaLocker ransomware removal. It is essential to remove WannaLocker ransomware from the smartphone or tablet to use normally again. To perform this task, we recommend that you install a mobile version of the anti-malware software and run a full system scan.
WannaLocker is designed to encrypt files on the external storage of the affected device. This unique technique was used by another mobile ransomware - SimpLocker. What's more, malware is designed to encrypt only files that do not begin with a ". Meanwhile, the files that are found in DCP, download, Dzeko, android and com director. Are not in the target field of the ransomware as well. Also, it does not encrypt files that are larger than 10 KB. There is currently no decryption software that can restore files encrypted by WannaLocker ransomware. However, if you back up your files, you can recover your files from them. But before that, you have to remove WannaLocker ransomware from the device.
It seems that the developers of WannaLocker are amateurs or wish to be found and arrested for cyber crimes. Cyber criminals do not ask to transfer the ransom to Bitcoins. Using alternative currency is popular among hackers because this way the money flow can not be tracked and criminals can not be found. But this time crooks request to transfer money using QQ, Alipay and WeChat which are popular payment methods in China. In addition, it is fairly easy to track the money flow and find people standing behind this cyber threat. In order to simplify payment, cyber criminals also provided two QR codes. All these amenities and small size (about 5-6 USD) should not motivate you to follow the hackers rules. They may not have decryption software or ask for more money. Even a small amount of money is a motivation for cybercriminals to develop new or improve current cyber threats. So do not sponsor them and just end WannaLocker ransomware of the device.
This mobile ransomware has been spotted spreading in Chinese gaming forums. It is presented as a plugin for the King of Glory (荣耀 荣耀) - a very popular game in China. The malicious file is named as "com.android.tencent.zdevs.bah. While users are misled and download this file, WannaLocker enters the device and begins its dangerous task. However, cyber-criminals could be using (or at least intend to use) other ransomware distribution channels. Therefore, you should be aware that malware could be distributed through malicious spam, malvertising, exploit kits, fake updates, phony software downloads, etc. Here are the most popular methods used by cyber -criminels. Therefore,
How to eliminate WannaLocker ransomware?
To remove WannaLocker ransomware from the Android phone or a tablet, the only one is to install a mobile antivirus program of the environment and to analyze the system using it. We recommend that you use Anti-Malware.
Learn how to remove WannaLocker ransomware from your computer
- Step 1. WannaLocker manual removal guide ransomware
- Step 2. Eliminate WannaLocker ransomware from browsers
Step 1. WannaLocker manual removal guide ransomware
A) Uninstalling Windows 8/7 / Vista
- Right click on the bottom left corner or click Start
- Choose Control Panel from the list
- Select Uninstall a program
- Choose the unwanted application and click uninstall
B) Uninstalling Windows XP
- Open the Start menu and select Panel
- Click Add or Remove Programs
- Choose the unwanted program, and then click Remove.
Step 2. Eliminate WannaLocker ransomware from browsers
A) Remove WannaLocker ransomware from Internet Explorer
- Click the gear icon and open Internet Options
- Replace your home page under the General tab
- Go back to the gear icon and select Manage add-ons
- In toolbars and Extensions, remove unwanted modules
- In search engines, end WannaLocker ransomware
- Choose a new search engine, and then click OK.
B) Removing Google Chrome's ransomware WannaLocker
- Click the Chrome menu
- Select more tools and go to Extensions
- Eliminate unwanted browser extensions
- Go to Settings, then choose Open Specific Page or Page Set
- Click on Set pages and choose a new homepage
- Click on Manage Search Engines under Search
- Delete WannaLocker ransomware and set a new search engine
C) WannaLocker ransomware removal from Mozilla Firefox
- Click on the menu icon (top right) and select Add-ons
- In Extensions, remove unwanted browser extensions
- Return to the menu and select Options
- On the General tab, change your home page
- On the Search tab, remove WannaLocker ransomware and set a new provider
Tags: cryptolocker,cryptolocker virus,virus cryptolocker,ransomware,malware,malware anti malware,ransom virus,ransomware protection,ransomware supprimer,ransomware solution,ransomware virus,ransomware definition,ransomware traduction,ransomware wannacry,ransomware kaspersky,ransomware removal,

























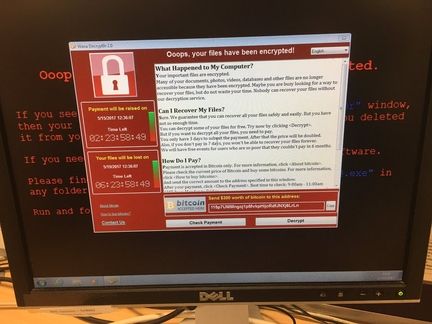 The unprecedented scale of this computer attack originated in a vulnerability of Windows exploited secretly by the NSA but whose existence had been revealed a few months earlier when hackers had made public some of the hacking and recovery tools Intelligence agencies.
The unprecedented scale of this computer attack originated in a vulnerability of Windows exploited secretly by the NSA but whose existence had been revealed a few months earlier when hackers had made public some of the hacking and recovery tools Intelligence agencies.