The value of network signal strength in smartphones may disappear with Android P
It seems that Google has communicated with mobile operators, and in Android P (9.0) will introduce a rather controversial change. It is about turning off the option of showing the signal strength of the network.
A group of people with XDA Developers found an intriguing change in the Android Open Source Project software, most likely enforced by a small group of American mobile operators. It's about a modification that in smartphones of selected operators in Android P (9.0) will allow you to hide the signal strength values. How does it work now?
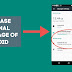
The value of the network signal power is shown in the settings of each Android smartphone (Settings -> About phone -> Information about the phone (Status) -> SIM card status) and is expressed in dBM. dBm is the logarithmic unit of measure of power related to the power of 1 mW. The power expressed in dBm informs about how much decibel this power is greater (or lower) than the power of 1 mW. For example: -100 dBM is a signal weaker than -77 dBM. This is illustrated by the graph below, on which you can see how many "bars" of the signal power illustrate a given signal strength range.
Most of you do not even pay attention to the signal strength, but it is a pretty good indicator of how the quality of connection with different networks on the same device looks like in different places. Alternatively, it gives a good view of the connection quality offered by different devices in the same place, using one SIM card. Why would the network operators want to hide this parameter? Here you can speculate forever.
The easiest way would probably be to assume that operators want to hide the signal strength due to shortcomings in their infrastructure. An uninformed user is in the end a user submitting fewer complaints about the service. In fact, no other rational explanation comes to my mind, and you?
Interestingly, the people responsible for finding changes informed that the programs enabling the measurement of the connection quality will continue to work properly, despite the introduced change. The signal strength will not be visible in the settings menu and can potentially be removed from the upper notification bar, but selected applications can still use the API and "pull" this information on top. The question is whether this function will not be blocked soon.
Source: XDA